 The fourth blog about the integration of Microsoft Intune and Lookout MTP we will have a look at the administrative side of things. We will have a look at what we are able to configure in relation to threats, we will have a look the devices that can be managed both in Lookout and how we need to setup compliance within Microsoft Intune.
The fourth blog about the integration of Microsoft Intune and Lookout MTP we will have a look at the administrative side of things. We will have a look at what we are able to configure in relation to threats, we will have a look the devices that can be managed both in Lookout and how we need to setup compliance within Microsoft Intune.
Lookout Admin Portal
The Lookout Admin Portal is accessible from https://aad.lookout.com, after you configured the consent like described in the last blog you are able to access. If you want to get a view of your current state of your devices, this is the place to be! The portal is divided into six workspaces;
| Workspace | Description |
| Dashboard | Get a direct view of the current status of your devices, how many devices are enrolled, how many are infected with what threat level and what king of source. Of course you will see the threats over time and all the numbers by category. |
| Threats | See active and resolved threats, you are allowed to create filters to get the right export for your management or security officer. Click on threats to get more information. |
| Devices | See all active and pending devices with the current threat levels. Click on the devices to get information about the device and active or resolved threats. |
| Policy | See what threat categories Lookout is able to detect and configure the severity of the threat to Low, Medium or High. Also iOS apps can be whitelisted when sideloading apps |
| System | Configure not only the Intune connector but also thinks like what kind of alerts you want to receive as an admin. |
| Support | Link to the support website and ticket system of Lookout. |
Dashboard
The dashboard gives you an overview about the state of your devices that are protected by Lookout for Work. Lookout for Work reports its status to the Lookout service and the gathered information will be shown. Get an easy overview of the device deployment, devices that are at risk, active threats and see trends about application threats, file threats, network threats and OS threats.
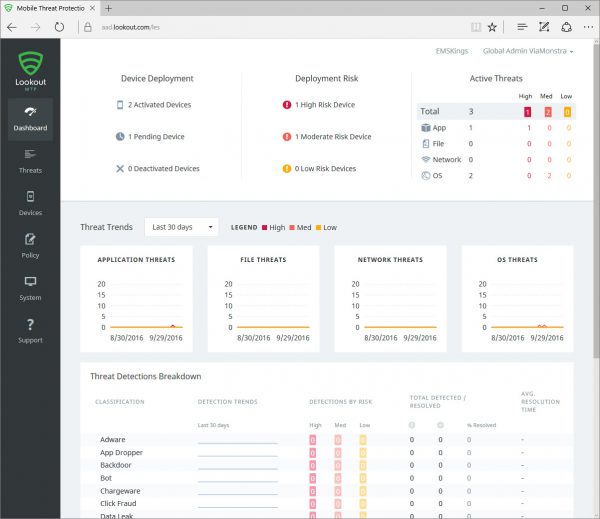
Threats
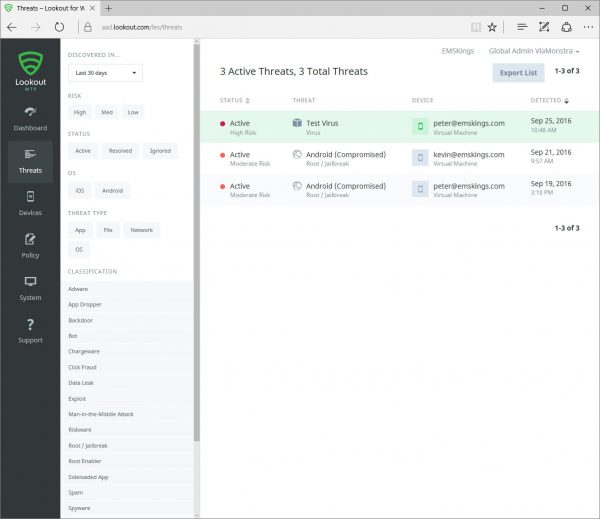
Looking at the Threats in the threats workspace of the Lookout web-console you can easy filter threats based on risks, status, OS, threat types and classifications. By default, all active, resolved and ignored threats of the last 30 days are shown. Since no threat records are removed you are able to show all the historical threats from your company.
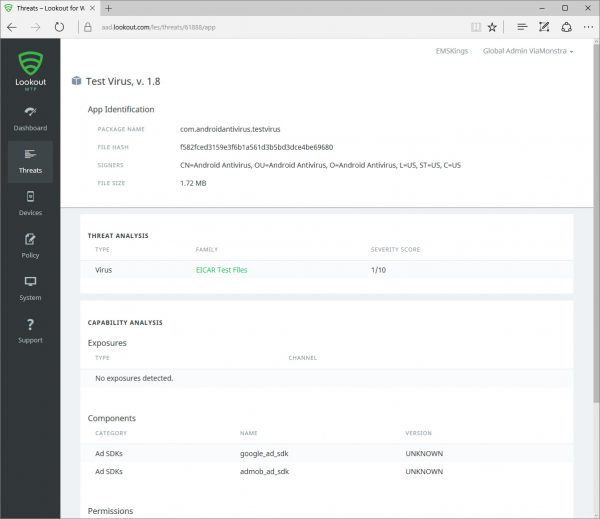
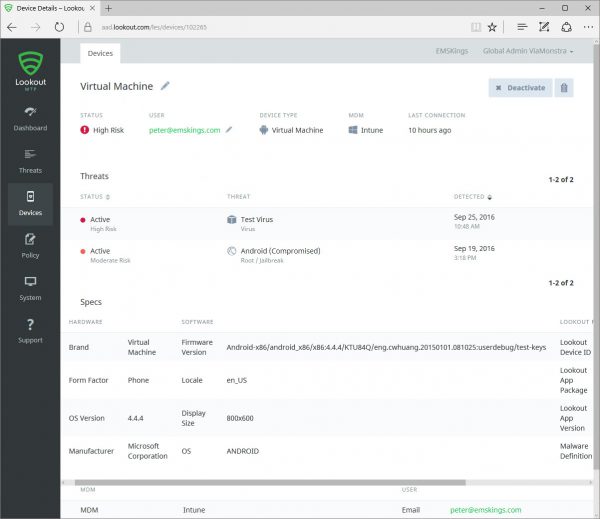
Clicking on an active (or resolved/ignored) threat gives you information about the threat on the device. This way you know what the impact can be and what is potentially happened with the device. Also binary analysis provided by Lookout can be accesses and analyzed.
This view gives you also an overview of the history of the threat in your environment.
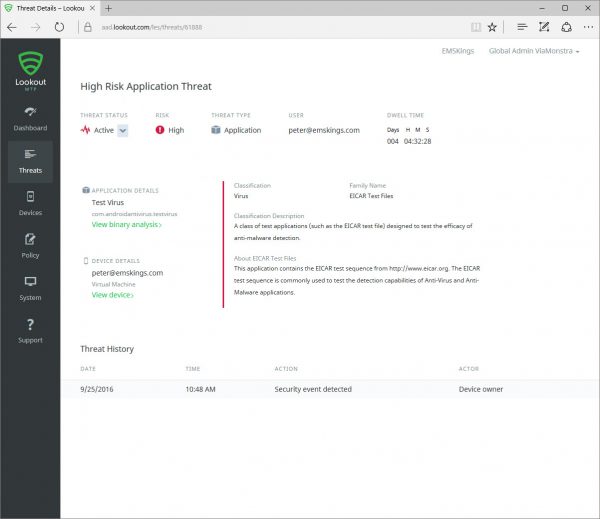
Looking at the binary analysis will give us information about the app itself and the threat analysis which can help you assessing if the detected threat is one that needs to be resolved immediately or not.
Devices
The devices workspace gives us a real time overview of the devices that are managed and gathered from Intune by Lookout. The devices can have different states;
| State | Description |
| Secured | Device is protected by Lookout, no threats are detected |
| Activated | Lookout for Work is activated |
| Pending | Device is gathered from Intune and user needs to install and/or active Lookout for Work. |
| Deactivated | Lookout for Work is deactivated from the Lookout MTP console. For instance when user leaves company. |
| Low Risk | A low risk is detected on the device and the risk is still active. |
| Medium Risk | A medium risk is detected on the device and the risk is still active. |
| High Risk | A high risk is detected on the device and the risk is still active. |
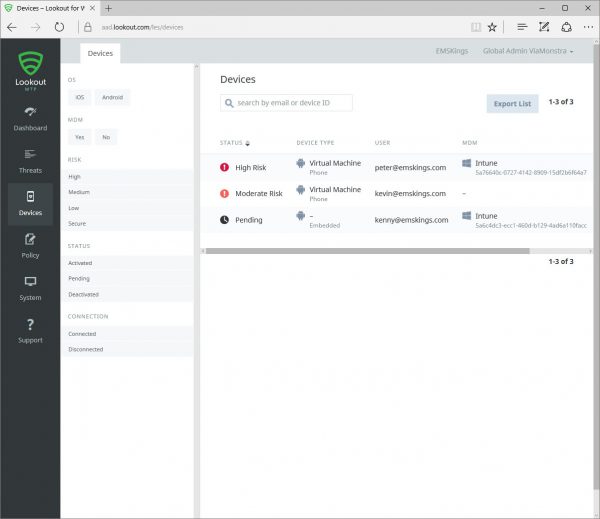
Besides the current state the device type, the UPN that is used to activate Lookout for Work and if the device is managed by Intune is displayed.
When clicking on a device, more information about the device itself, the installed Lookout for Work app and the threat history can be found. Per threat more information can be gathered like in the threat workspace.
Policy
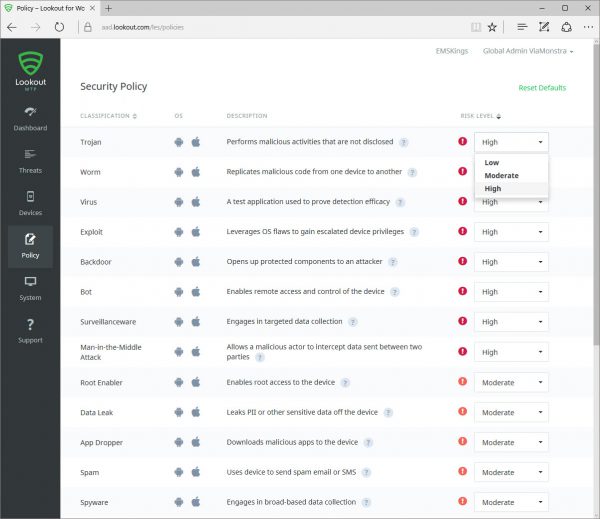
The risk levels of the policy categories like listed in the first blog of this series can be configured to be Low, Medium or High, like shown below. This way you are able to create custom protection for your company.
For iOS apps can also be whitelisted so that custom Line Of Business apps can be side loaded via Microsoft Intune.
System
The System workspace is the place to be to configure the Lookout Mobile Threat Protection cloud service. In the third blog I showed how to setup the connector between Microsoft Intune and Lookout MTP.
The System workspace is devices in several tabs;
| Tab | Description |
| Account | See the information about your subscription and the current license usage by your company. |
| Admin | All administrators and restricted administrators are listed that are member of the Azure AD groups that were created in the last blog. |
| Enrollment | Configure the language of the console and when a device is considered as disconnected. By default a device is considered as disconnected when Lookout did not contact the service for 30 days. |
| iOS | For iOS an iPA file needs to be downloaded and signed with your Apple Enterprise Developer certificate. (will cover this in the last blog of this series) |
| Connectors | Create and configure the connector for Microsoft Intune. |
| Preferences | Configure if you as an admin wants to receive emails when a Low, Medium and/or High threat is detected. This needs to be configured per admin and all levels are selected by default. |
Microsoft Intune side
In Intune not much needs to be done besides by pushing the Android and iOS Lookout for Work Apps as required apps for the mobile devices and the maximum allowed threat level in the Compliance Policy needs to be configured.
In the Compliance Policy that needs to be deployed to all users that need to use Lookout for Work you need to configure one of the following maximum allowed threat levels;
| Threat level | Description |
| None (secured) | No threat is allowed, if a low threat or higher is detected the device will be considered as non-compliant and all access to apps (like Exchange Online, SharePoint Online, Skype for Business Online, CRM Online, Exchange on-premises) that use Conditional Access is blocked. |
| Low | Only low threats are allowed to keep the device compliant. |
| Medium | Only low and medium threats are allowed to keep the device compliant. |
| High | All threats are allowed to keep your device compliant. |
In the next blog we will have a look at the end user experience, remember to be able to use the integration of Lookout with Intune you need a separate Lookout MTP license.
Other blogs in this series:
- Integration Microsoft Intune and Lookout Mobile Threat Protection is there
- Intune and Lookout: the architecture of the integration
- Intune and Lookout: how to integrate?
- Intune and Lookout: the admin experience.
- Intune and Lookout: the end user experience.
- Intune and Lookout: supporting iOS devices
- Intune, ConfigMgr and Lookout better together


