Last year Microsoft was planning to mark devices that were not evaluated by a compliance policy as non-compliant. The default behavior is that if a device is not evaluated by a compliance policy that it is being marked as compliant and therefor the user has access to services controlled by Conditional Access in Azure AD, which could be lead to compliance issues.
After feedback from customers Microsoft decided to push back the change so that the current customers would not be impacted. The last release of Microsoft Intune now allows us to configure what Microsoft Intune needs to do when no compliance policy is assigned.
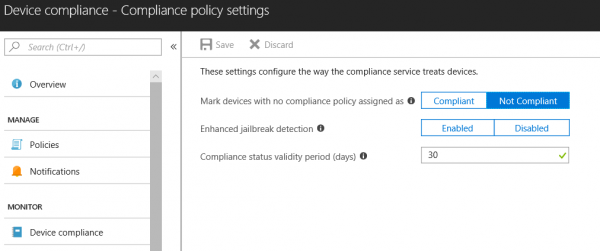
As an Administrator you are now able to choose if a device is automatically marked as compliant or marked as non-compliant when no compliance policy is assigned.
When using Conditional Access in Azure AD (which you should), you are able to block access to Office 365 services or applications on Azure for non-compliant devices. The default option is Non Compliant. So be sure to change it if you do not want your devices to be marked as non-compliant.

In the figure above, you see also a new option called Enhanced jailbreak detection. When enabling this option iOS devices will check in more often to the Microsoft Intune service to evaluate the compliance state of the jailbreak states of the device at least every 72 hours. This option uses the location service of the device, which could impact the battery life of the device.



Hi Peter,
For the mass majority of our mobile devices, we will want to use a MAM-WE model for managing corporate data, without taking full management of the devices. In our case, is it necessary to mark devices with no compliance policy assigned as Compliant?
Otherwise, my understanding is that we’d have to apply a Device Compliance Policy to any device we want to access corporate data, and that means taking management of the device. We only care about keeping our data sandboxed and secured in the managed apps, and being able to wipe that data if needed.
Anytime I am changing a global setting that takes a less secure posture than Microsoft’s recommendations, I want to make sure it’s absolutely necessary. Am I right on this or is there another way to get to where we want to be that I’m missing?
Thank you