The App Protection Policies in Microsoft Intune are used to protect corporate data in apps that have the Intune SDK integrated. During the last service update of Microsoft Intune some nice new features were added to the policy set.
While accessing a by Microsoft Intune managed app, the device can be checked if for instance a device is rooted or jailbroken, or what kind of OS version is on the device while launching the app on the device, based on the results we are now able to add an action, sometimes multiple actions. So you are able to based on a setting, block access, warn the user or wipe the company data in the app.
Lets see how this looks like.
New App Protection capabilities on iOS
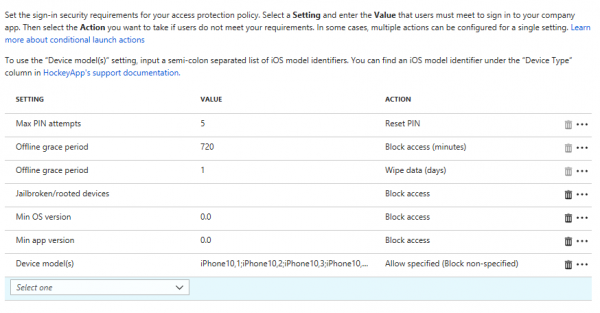
Below you find an overview of the checks and (automatic) actions for App Protection policies on iOS;
| Setting | Action |
| Max PIN Attempts | Reset PIN Wipe data |
| Offline grace period | Block access Wipe data |
| Jailbroken / rooted devices | Block access Wipe data |
| Min OS version | Block access Wipe data Warn |
| Min App version | Block access Wipe data Warn |
| Min SDK version | Block access Wipe data |
| Device Model(s) | Allow specific (block non-specific) Allow specific (wipe non-specific) |
When a device is “not compliant” with one of the settings, the action will be performed instantly. So for instance a user jailbreaks the device, the corporate data is automatically wiped.
During the service update we also have now the ability to check what model of device is being used to access the corporate data. In the example below, I only allow iPhone 8 and iPhone X devices to access our corporate email. See a complete list of models that can be used via this link.
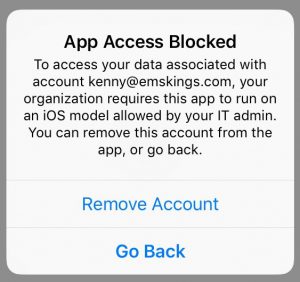
The end user experience looks like below. The user is not able to access their email and can remove the account or contact their administrator.
New App Protection capabilities on Android
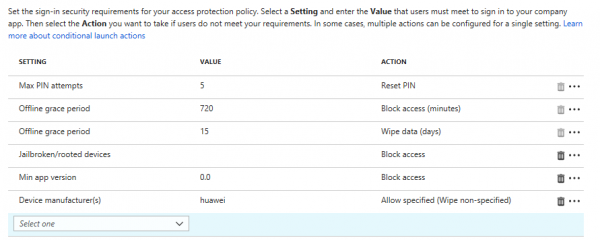
On Android there are also additions, below you find an overview of the checks and (automatic) actions for App Protection policies on Android;
| Setting | Action |
| Max PIN Attempts | Reset PIN Wipe data |
| Offline grace period | Block access Wipe data |
| Jailbroken / rooted devices | Block access Wipe data |
| Min OS version | Block access Wipe data Warn |
| Min App version | Block access Wipe data Warn |
| Min patch version | Block access Wipe data |
| Device Manufactures(s) | Allow specific (block non-specific) Allow specific (wipe non-specific) |
New to the Android App Protection policy is that we now can “whitelist” device manufactures of devices that can be used to access the corporate data via the Intune managed apps.
In the example below, I only allow devices manufactured by Huawei to access our corporate email. (don’t ask me why ???? ). In this case the data should be wiped instantly.
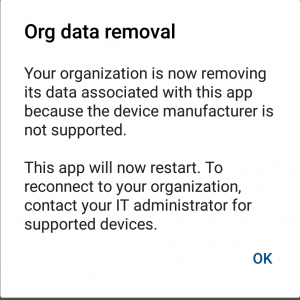
The end user experience looks like below. The user is not able to access their email and can remove the account or contact their administrator.
Another great example of the innovation that is constantly added to Microsoft Intune.
Till next time!



I used the minimum OS version attribute for some public apps like Microsoft Outlook but the app protection policy doesnot kick in. I deployed this policy to a user group which I am part of.