 The mobility space is an area that is moving fast, almost every day new products, new features or complete new versions of Operating Systems are released. As a mobile device Administrator it is your job to secure the mobile devices and the corporate data on it, but also when you are like me being part of a project implementing Microsoft Intune as the MDM solution in an environment where data leakage prevention is very important. We need to set the baseline and be aware of the changing variables.
The mobility space is an area that is moving fast, almost every day new products, new features or complete new versions of Operating Systems are released. As a mobile device Administrator it is your job to secure the mobile devices and the corporate data on it, but also when you are like me being part of a project implementing Microsoft Intune as the MDM solution in an environment where data leakage prevention is very important. We need to set the baseline and be aware of the changing variables.
It is easy when you only allow corporate owned devices to be able to connect to your environment, it becomes challenging when allowing Bring Your Own Devices. The market is huge and the diversity of operating systems and devices is enormous!
BYOD versus CYOD
Lately I hear a lot of stories that BYOD is history and that companies are shifting to Choose Your Own (corporate) Device (CYOD), a user is able to choose based on their budget from a list of approved (whitelisted) devices. I think this is a good option if you, as an administrator want to be in control and you want to be sure that you are able to perfectly support the connected devices. Maybe currently the ideal world, but still the majority of the devices are still BYOD and no CYOD. So we need to do some more.
BYOD is still massive, so how to cope with new features/platforms?
Since BYOD is still a fact you need to know that the devices that are able to connect we need to cope with it and if you ask me only support platforms and versions you have tested. At least that would be my advice. Why? Okay let’s share a short story about a great usability feature on Android can bypass all of your passcode related features. The feature is called Android Smart Lock.
A while ago we came across a great feature of Android 5.x called Android Smart Lock. Android Smart Lock basically allows users to bypass the passcode security policies based on a location (trusted place), trusted device (Bluetooth device), trusted voice or via on-body detection (heartbeat). Superb for the user experience but a nightmare if you want to protect your device and its data!
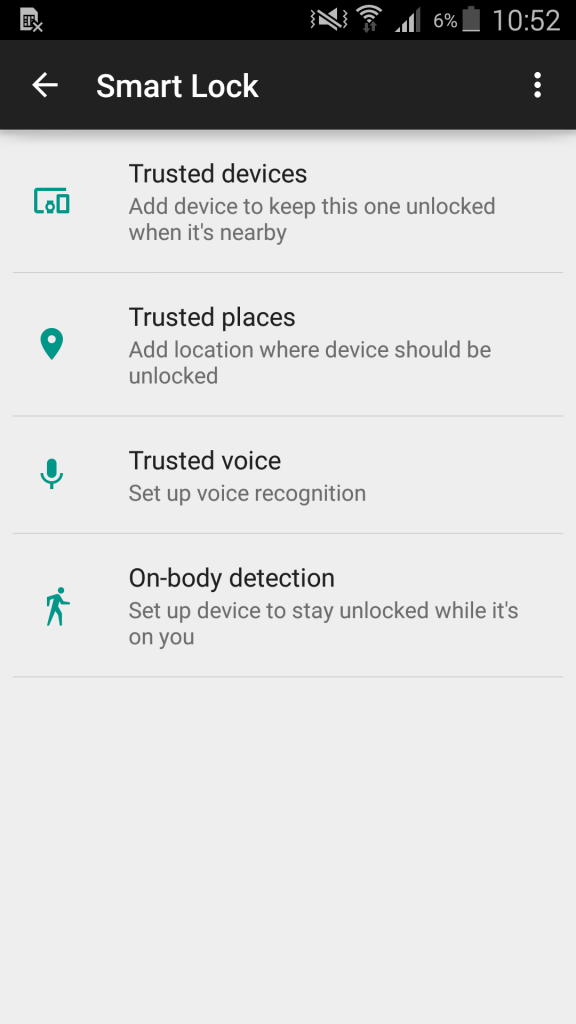
Like shown below you are able to add trusted locations to Google Smart Lock and bypass every security measurement you configured. So on the configures locations a user does not have to enter a PIN or passcode……
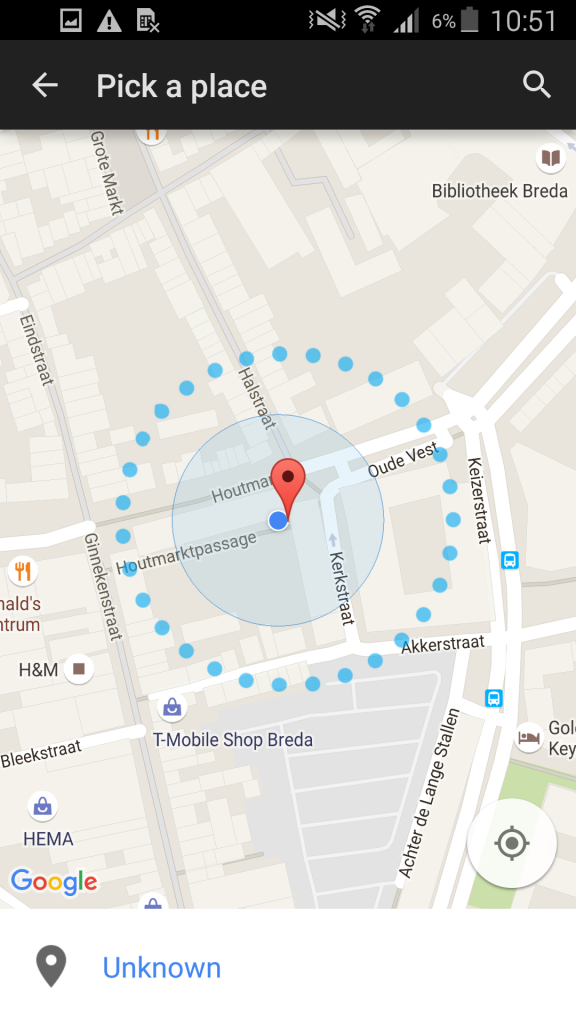
Currently not every MDM vendor is capable to manage this Android Smart Lock feature, so this may currently be a security risk without knowing it and if you do not do anything. I know that for instance MobileIron does not have this yet. Users are able to bypass the first line of defense, the device passcode/password.
The good thing of Intune standalone or connected with Configuration Manager is that Microsoft is able to really react quickly on new features of platforms and almost every time is able to give zero-day support for new operating systems.
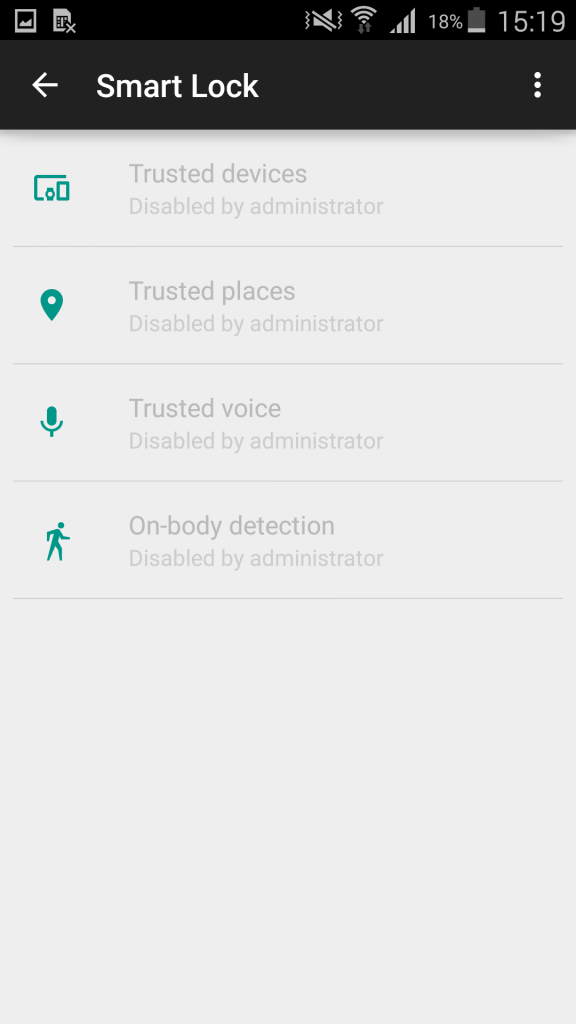
That being said you always need to validate the new security policies and new features of new operating systems before allowing them to connect to your environment. How? That is fairly easy!
Conditional Access based Operating System version is the solution!
Like the other MDM vendors Microsoft Intune and Intune together with Configuration Manager has a capability to have conditional access based on operating system versions. So the ideal option is to only support what you know, what you have validated and what you have tested. It is really important to implement something like Life Cycle Management and determine the lowest AND highest version of an Operating System you want to support!
So until you have validated for instance a new release of Android, just block everything below and above the versions.
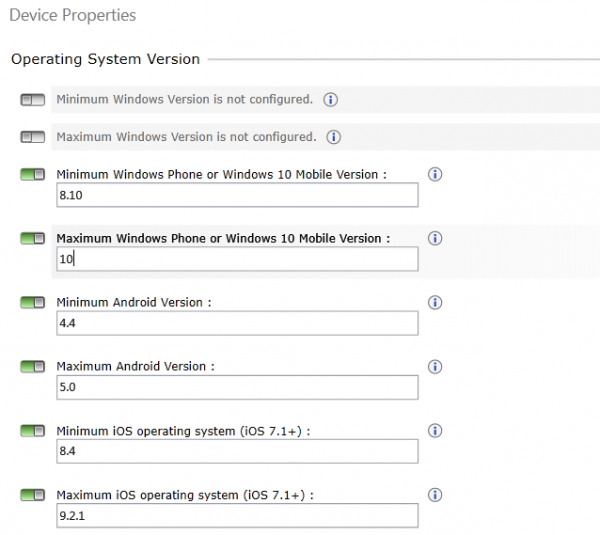
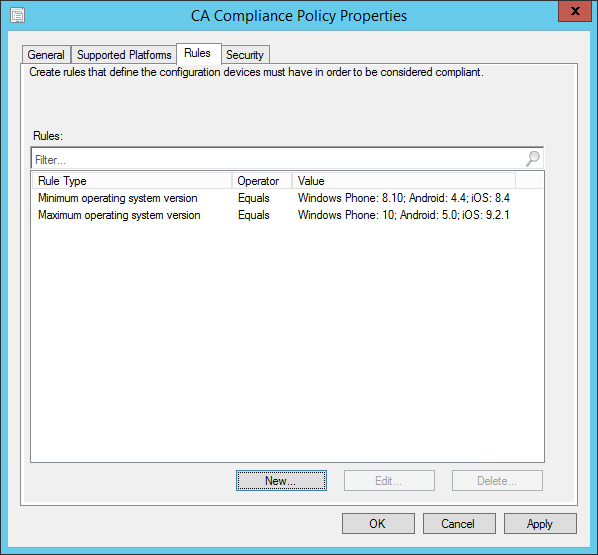
If a device is not does not comply to your configured values the users will not have access until you have assessed the new operating system and configured the new policies when they are available. In other words, you are back in control.
In order to be able to test and verify the new versions asap, you are able to join test programs which allows you to test beta builds or technical previews of the new operating systems;
- Windows Mobile: http://ref.ms/insiders
- iOS Beta program: http://ref.ms/isobeta
- Android Beta program: (depends on hardware provider)
So what are your thoughts on this? Let me know!


